The Website Security Module provides a comprehensive overview of the website’s security posture. It includes organization external surface analysis, port status, and identified external vulnerabilities on your websites/web apps etc. This module helps in detecting potential threats, misconfigurations, and exposure points, ensuring proactive security measures are in place.

This section categorizes the website's vulnerabilities into various severity levels, providing a detailed breakdown of potential risks and their impact. The severity levels are defined as follows:
Critical: Risks that pose an immediate and severe threat to the website's functionality, security, or data integrity. These vulnerabilities could lead to complete system compromise, data breaches, or significant downtime. Immediate action is required to mitigate these risks.
High: Risks that have a substantial impact on the website's security or performance but may not be as immediately threatening as critical risks. These vulnerabilities could lead to unauthorized access, data leakage, or significant operational disruptions. Prompt attention and remediation are necessary.
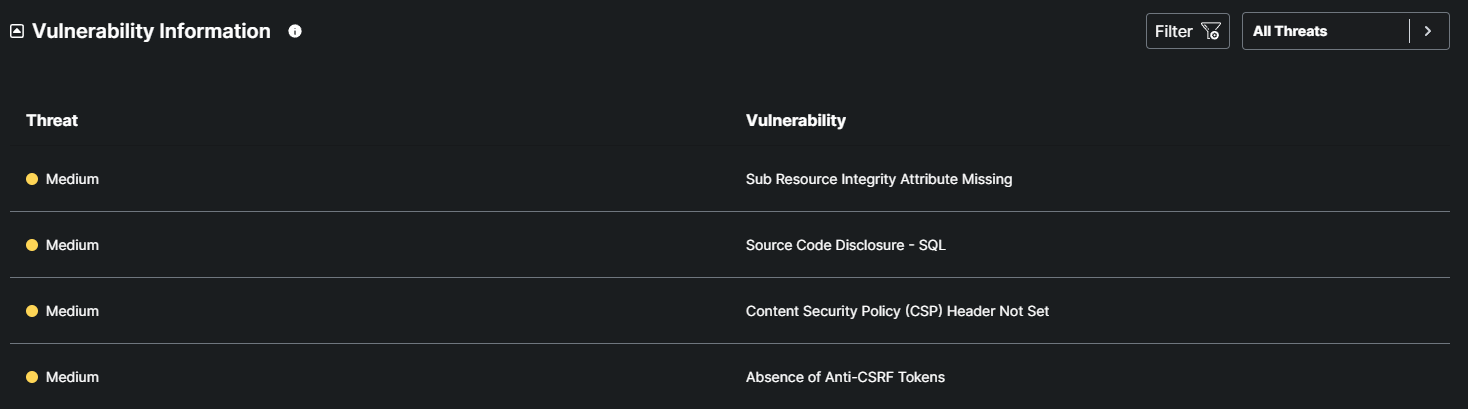
Medium: Risks that present a moderate level of threat to the website. These vulnerabilities may not have an immediate impact but could be exploited under certain conditions, potentially leading to limited data exposure or minor operational issues. These should be addressed in a timely manner.
Low: Risks that have a minimal impact on the website's overall security or performance. These vulnerabilities are typically harder to exploit and may only result in minor inconveniences or limited information disclosure. While not urgent, these should still be monitored and resolved as resources allow.
Informational: These are not actual risks but rather observations or findings that provide useful context about the website's configuration, performance, or security posture. They do not pose a direct threat but can offer insights for optimizing the website's security and functionality.
This section provides a comprehensive analysis of the website's external attack surface, including Web Application Firewall status, company domains, lookalike domains and status of SSL Certificates.
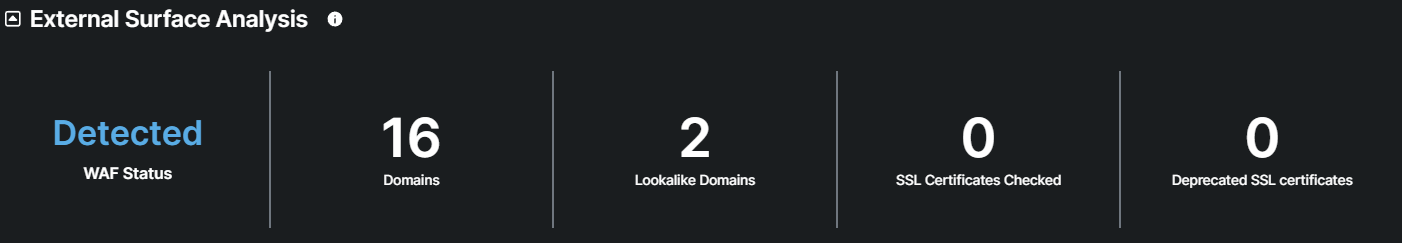
Indicates whether a WAF is actively deployed and protecting the website.

This Number provides a detailed inventory of all active subdomains associated with the primary domain.
A list of domains that closely resemble the primary domain. Lookalike domains are a common tool used in typosquatting attacks, where malicious actors register domains that closely resemble legitimate ones to deceive users. These domains can be used for phishing, credential theft, malware distribution, or fraud. Monitoring and identifying lookalike domains helps organizations proactively protect their brand, customers, and employees from cyber threats by preventing unauthorized impersonation and mitigating potential security risks before they cause harm.
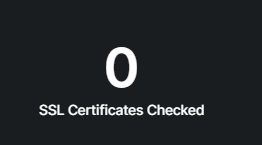
A list of domains and subdomains with valid SSL/TLS certificates.
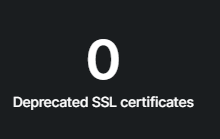
A list of domains or subdomains with expired SSL certificates, can lead to browser warnings and loss of user trust.
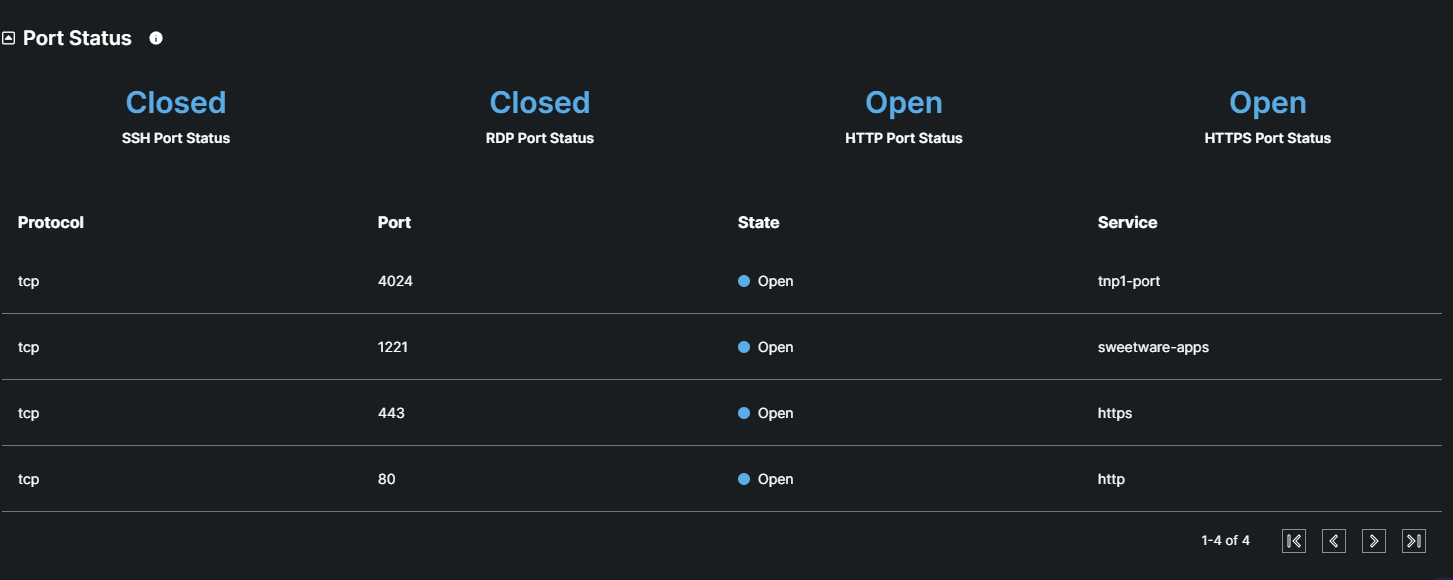
This table provides a detailed overview of the status of ports associated with the website's external surface, including whether they are open, closed.
This table offers a comprehensive overview of detected vulnerabilities. Each row presents the severity level (critical, high, medium, low, or informational) along with the specific name of the vulnerability.